BREAKING NEWS
LATEST POSTS
-
Q2 2024 Global Production Report
https://prodpro.com/blog/q2-2024-global-production-report/
What’s important: Over the past 6 months, the total number of productions filming globally in 2024 is still 16% lower than in 2022, and 37% lower in the US.
Why it matters: The lower volumes are here to stay.
-
Supersplat – Online open source Gaussian Splats ply viewer
FEATURED POSTS
-
Top 3D Printing Website Resources
The Holy Grail – https://github.com/ad-si/awesome-3d-printing
- Thingiverse – https://www.thingiverse.com/
- Makerworld – https://makerworld.com/
- Printables – https://www.printables.com/
- Cults – https://cults3d.com/
- CG Trader – https://www.cgtrader.com/3d-print-models
- Sketchfab – https://sketchfab.com/store/3d-models/stl
- 3D Export – https://3dexport.com/
- MyMiniFactory – https://www.myminifactory.com/
- Thangs – https://thangs.com/
- Yeggi – https://www.yeggi.com/
- FAB365 – https://fab365.net/
- Gambody – https://www.gambody.com/
- All3DP News – https://all3dp.com/
- TCT Magazine – https://www.tctmagazine.com/topics/3D-printing-news/
- 3DPrint.com – https://3dprint.com/
- NASA 3D Models – https://nasa3d.arc.nasa.gov/models/printable
-
Photography basics: Shutter angle and shutter speed and motion blur
http://www.shutterangle.com/2012/cinematic-look-frame-rate-shutter-speed/
https://www.cinema5d.com/global-vs-rolling-shutter
https://www.wikihow.com/Choose-a-Camera-Shutter-Speed
Shutter is the device that controls the amount of light through a lens. Basically in general it controls the amount of time a film is exposed.
Shutter speed is how long this device is open for, which also defines motion blur… the longer it stays open the blurrier the image captured.
The number refers to the amount of light actually allowed through.As a reference, shooting at 24fps, at 180 shutter angle or 1/48th of shutter speed (0.0208 exposure time) will produce motion blur which is similar to what we perceive at naked eye
Talked of as in (shutter) angles, for historical reasons, as the original exposure mechanism was controlled through a pie shaped mirror in front of the lens.
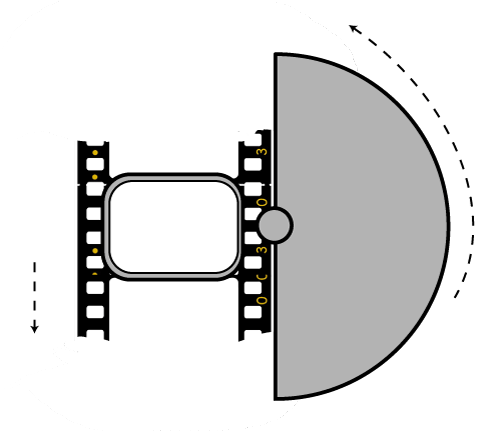
A shutter of 180 degrees is blocking/allowing light for half circle. (half blocked, half open). 270 degrees is one quarter pie shaped, which would allow for a higher exposure time (3 quarter pie open, vs one quarter closed) 90 degrees is three quarter pie shaped, which would allow for a lower exposure (one quarter open, three quarters closed)
(more…)